In an era where data breaches and cyber threats dominate headlines, organizations are being challenged to safeguard sensitive information as never before. One powerful tool in this fight against data breaches and ransomware is data encryption.
While the practice of encrypting data in-transit and at-rest has become common practice, these encryption strategies do not address the most common point when data is vulnerable and stolen: when the data is being used. That’s why the crucial data encryption technology that must be included is encryption in-use.
Many people do not know that encryption in-use even exists, or that it alone can protect the data where it is most vulnerable. This article delves its significance and how it is the missing link in most data security strategies.
The Evolving Threat Landscape
The digital landscape is rife with evolving threats: sophisticated cybercriminals, state-sponsored hacking, software security bugs and even employees pose a risk. As technology advances, so do the methods employed to exploit vulnerabilities and steal or ransom data.
Understanding Data Encryption in-Use
Encryption in use, also known as homomorphic encryption, refers to the protection of data while it is being processed or used by applications. Traditional encryption methods secure data when it is stored (at-rest) or while it is in transit between systems (in-transit). However, when data is actively being used, such as during search, computations, or analyses; it is only protected by perimeter security that is notoriously vulnerable. Systems that only encrypt in-transit and at-rest provide zero protection when the data is in use.
The Perils of Only Encrypting in-Transit and at-Rest
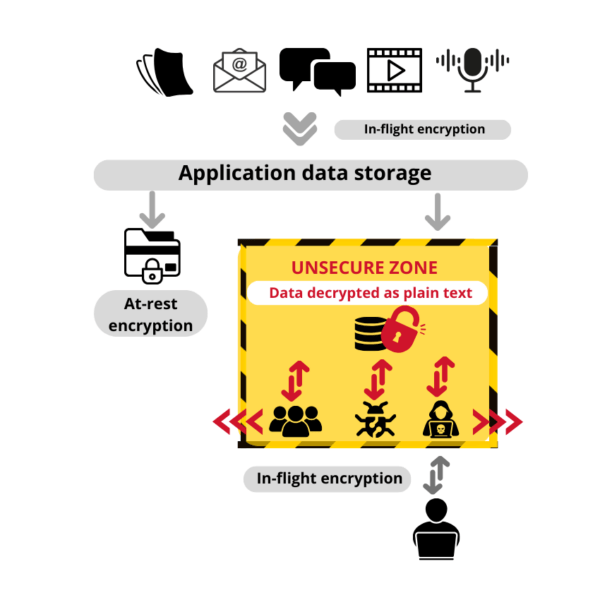
When data is encrypted at rest, there are two copies made of the data. One copy is encrypted, but one copy is saved in clear text. (See Figure 1) Why? Because without encryption in-use technology, the only way data can be searched is via clear text. Clear text data can be easily removed from the system and data clearly seen in this most vulnerable state.
Benefits of Encryption in-Use
Encryption in-use addresses the “Unsecure Zone” outlined in Figure 1. It does his by keeping the data encrypted while the data is being used, providing true end-to-end protection. (See Figure 2).
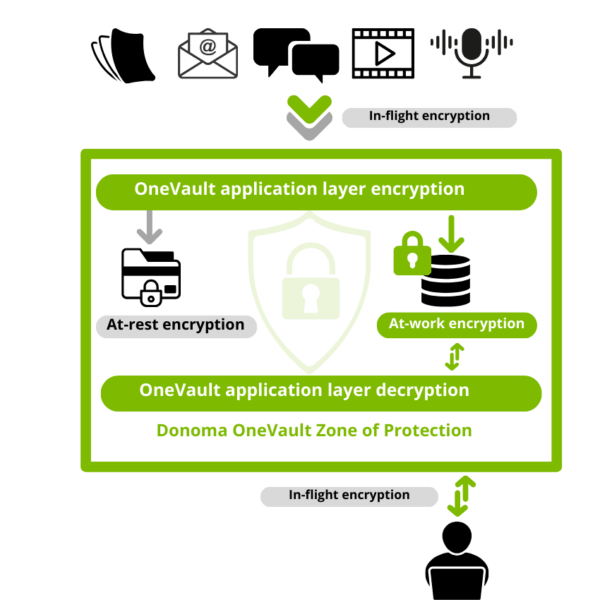
Encryption in-use “scrambles” the data (what we call hashed data) that would be undecipherable if anyone without the correct encryption keys were to try and access the data.
This comprehensive level of data security drives powerful outcomes that are becoming a high priority for every organization:
1. Ensure Data Security & Integrity
Encryption in-use ensures that data is secure and preserved for the duration of its designated lifecycle.
2. Secure & Preserve Customers with a Proactive Data Security Stance
Having a highly secure and accountable level of data security is a powerful tool for competitive differentiation. Those who take a proactive stance to innovate for differentiation will benefit both with much greater data security and the ability to build a reputation for safety that makes it possible to take/preserve market share.
3. Meet Regulatory Compliance and Legal Requirements
With ransomware’s ongoing fallout is driving a quickly expanding set of regulations around data security and data privacy protections. Now, almost every organization is now required to meet strict standards that mandate the auditable preservation, protection, and production of data. The reporting and production requirements alone are outpacing prior technologies such as cold-storage and backup because of the very short production timelines required. Organizations are now subject to audits to cross check how the data is secured. This on top of the expectation that a wider range of stakeholders be able access and leverage company data.
4. Address the Hardest Threat of All
The latest research from Gartner validates that the biggest threat to data security comes from staff. They make mistakes and take shortcuts to get jobs done sooner. Gartner quotes a finding from their research that 90% of employees admitted activities that would increase cyber risk — even though they knew this to be the case.Clearly, better guard rails must be enacted to address this reality. Encryption in-use prevents the exposure of sensitive information, whether that action is intentional or the result of poor credential management, technical skill gaps and other factors such as software vulnerabilities that often exacerbate these situations.
Conclusion
With the continuing escalation of ransomware and data exposure driving headlines as well as significant damages, prioritizing end to end encryption: from in-transit, in-use AND at-rest is not just a best practice; it’s a strategic imperative.
Encryption in-use is often perceived as being too difficult (and therefore expensive), and this has allowed partial encryption strategies to be good enough. The good news is that encryption in-use is no longer outside the technical or financial reach of any organization.
Next Steps: Gain the Security and the Cost Savings of up to 50% off Your Current Solution
If your organization is looking to strengthen your information security posture, update your information governance to include a broader range of application data and be better prepared for audits, we’d like to talk to you about Donoma OneVault. It provides powerful Information Governance and e-Discovery all secured with encryption in-transit, in-use and at-rest.
We understand that making a change seem stressful, but we have the expertise to streamline migrations and be operational in far shorter timeframes that traditional deployments. Plus, we are offering incentives to significantly reduce your costs with competitive buyouts that reduce your current spend by up to 50%. We challenge you: if you could get more security and save up to 50%, is that worth a no-obligation conversation? We think you have nothing to lose, and everything to gain.
Schedule a solution demo today, and we’ll show you how Donoma OneVault will not only provide a higher standard of security, but incredible performance and real budget savings.
SCHEDULE A DEMO
Additional Resources
Information Governance Best Practices to Strengthen Cyber Security


