When you think about data breaches, your mind probably goes to healthcare systems, financial institutions, or social media platforms. But there’s a growing vulnerability sitting in your driveway right now; and the recent Hyundai breach demonstrates exactly why we need to start paying attention.
The Hyundai Wake-Up Call
In early November 2025, Hyundai AutoEver America (HAEA) notified up to 2.7 million Hyundai, Kia, and Genesis customers that their most sensitive personal information had been compromised. The exposed data included names, addresses, phone numbers, driver’s licenses, and, most alarmingly, Social Security numbers.
The breach timeline reveals a troubling pattern: unauthorized access began on February 22, 2025, and continued until March 2 when HAEA detected and expelled the intruders. Yet customers weren’t notified until late October—more than seven months after the breach was contained. Cybercriminals had ample time to exploit stolen data, cross-reference it with information from other breaches, and craft highly targeted fraud schemes.
This marks Hyundai’s third major breach in three years, following similar incidents in Europe in 2023 and 2024: a pattern that suggests systemic vulnerabilities rather than isolated security lapses.
Your Car Knows More About You Than You Think
Modern vehicles are no longer simply machines that get you from point A to point B. They’re sophisticated data collection platforms on wheels. Every connected car service, every diagnostic report, every navigation query—all of it generates data that gets stored, processed, and transmitted through automotive IT infrastructure.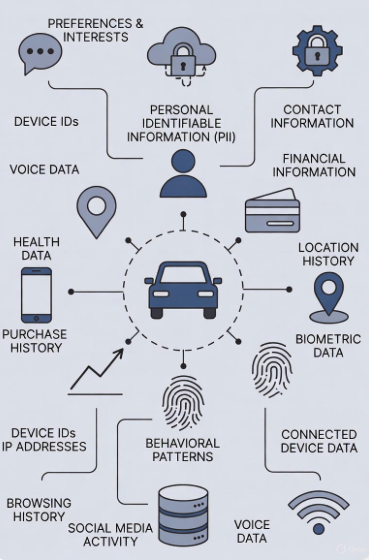
Consider what automotive systems now collect:
- Personal identification data: Names, addresses, contact information, Social Security numbers, driver’s license details
- Financial information: Payment methods for in-car purchases, subscription services, toll payments
- Location history: Every destination you’ve searched, every route you’ve taken, patterns of where you go and when, even your saved locations like your home’s location
- Biometric data: Voice recordings from voice-activated systems, facial recognition for driver monitoring systems
- Behavioral patterns: Driving habits, acceleration patterns, preferred routes, vehicle usage schedules
- Connected device data: Smartphone contacts, call logs, text messages synced to your vehicle’s infotainment system
The intimacy of this data cannot be overstated. Your car knows where you work, where your children go to school, where you seek medical care, where you worship, where you shop, and where you spend your leisure time. Combined with your Social Security number and driver’s license, as happened here, this creates a rich profile that can be weaponized for identity theft, stalking, targeted phishing, financial fraud, or worse.
The Current and Future Impact of Automotive Data Breaches
Immediate Consequences
When automotive data breaches occur, the immediate impacts are significant and long-lasting:
Identity Theft: Unlike passwords that can be changed or credit cards that can be canceled, Social Security numbers are permanent identifiers. Once compromised, they provide a foundation for synthetic identity fraud that can persist for years.
Targeted Phishing Campaigns: Cybercriminals can use detailed personal information to craft convincing phishing emails or phone calls. “We’re calling from Hyundai regarding your 2023 Tucson that you purchased at [specific dealership]” sounds far more legitimate than generic scam attempts.
Financial Fraud: Combined data sets allow criminals to open fraudulent accounts, file false tax returns, apply for loans, and commit other forms of financial fraud that can devastate victims’ credit and financial standing.
Physical Security Risks: Location data combined with personal schedules can enable physical crimes. Knowing when someone is consistently away from home, combined with their address, creates opportunities for burglary.
The Escalating Threat Landscape
As vehicles become more connected and autonomous, the data vulnerability only intensifies:
Vehicle-to-Everything (V2X) Communication: Future vehicles will communicate with infrastructure, other vehicles, and cloud services in real-time, exponentially increasing data transmission volumes and potential attack surfaces.
Over-the-Air Updates: While convenient, OTA update capabilities create additional entry points for attackers if not properly secured.
Autonomous Vehicle Systems: Self-driving cars will generate and process massive amounts of sensor data, including detailed 3D mapping of neighborhoods and continuous video/LIDAR recordings of public spaces.
Insurance Telematics: Usage-based insurance programs collect granular driving behavior data, creating detailed profiles that, if breached, could be used for discrimination or manipulation.
The automotive industry’s cybersecurity challenges are compounded by the fact that vehicles have 15-20 year lifespans. Security vulnerabilities in systems designed today will persist on the road for decades.
The Encryption Gap in Automotive IT Infrastructure
Here’s the uncomfortable truth about the Hyundai breach and most data breaches like it: the stolen information was likely encrypted when stored “at rest” in databases and encrypted “in transit” when transmitted over networks. Hyundai AutoEver America almost certainly had standard security measures in place.
But there’s a critical vulnerability window that traditional encryption doesn’t address: when data is actively being processed.
To perform necessary operations, customer service lookups, system diagnostics, data analytics, machine learning model training, the data must be decrypted. During these processing windows, which can last milliseconds or hours depending on the operation, the data sits unencrypted where attackers can steal it.
This is what we call the “encryption gap”, and it’s exactly what attackers exploited when they had access to HAEA’s IT environment.
A Comparative Scenario: Traditional Security vs. Continuous Encryption
How the Breach Unfolded with Traditional Security
Day 1 (February 22): Attackers gain unauthorized access to HAEA’s IT environment through an unknown vector—possibly compromised credentials, a software vulnerability, or social engineering.
Days 1-9: With network access established, attackers navigate HAEA’s systems, identifying databases containing customer information. When legitimate system processes decrypt data for routine operations: generating service reports, processing warranty claims, analyzing customer trends, the attackers intercept this unencrypted data.
Day 8 (March 1): HAEA’s security monitoring detects unusual activity and launches an investigation.
Day 9 (March 2): Attackers are expelled, but by this point they’ve exfiltrated names, Social Security numbers, driver’s licenses, and other sensitive data for millions of customers.
Months Later: Despite the breach being contained in early March, the forensic investigation takes months to determine the full scope. Customers aren’t notified until late October, seven months after containment, while their compromised data circulates in criminal markets.
How It Could Have Been Different
Now imagine this same scenario, but with Hyundai AutoEver America using Seshat’s continuous encryption technology:
Day 1 (February 22): Attackers gain the same unauthorized access through the same vulnerability. They navigate the network and identify the same databases.
Days 1-9: Here’s where everything changes. When system processes need to perform operations on customer data, generating reports, running analytics, processing service requests, those operations happen while the data remains encrypted.
With Seshat’s next-generation homomorphic encryption implementation, mathematical operations, machine learning inference, and data analysis occur directly on encrypted data. The system never decrypts Social Security numbers, driver’s licenses, names, or addresses during processing. Even with full network access, the attackers see no data.
Day 8 (March 1): HAEA’s monitoring still detects the intrusion and launches the same investigation.
Day 9 (March 2): Attackers are expelled, but they leave empty-handed. Despite having the same access and spending the same nine days in the network, they’ve captured nothing but encrypted data that’s computationally infeasible to break.
Result: No customer notification required. No credit monitoring services needed. No class action lawsuits filed. No regulatory penalties imposed. No reputational damage suffered. The breach attempt becomes a non-event from a data exposure perspective.
Continuous Encryption Changes Everything for Automotive IT
The implications of continuous encryption extend beyond preventing breaches:
Regulatory Compliance: With regulations like GDPR, CCPA, and emerging automotive cybersecurity standards, continuous encryption provides the strongest possible technical safeguard, potentially reducing liability in the event of security incidents.
Customer Trust: In an era where automotive brands are competing on data privacy and security, demonstrating that customer data remains encrypted even during active use provides meaningful differentiation.
Operational Resilience: Security teams gain breathing room to detect and respond to intrusions without the immediate crisis of “data in the wild” that forces rushed notifications and emergency response.
Cost Avoidance: The average cost of a data breach now exceeds $4.5 million, not including long-term reputational damage, lost customer lifetime value, and potential criminal exposure. Preventing the breach is dramatically more cost-effective than managing its aftermath.
Zero Trust Architecture: Continuous encryption aligns perfectly with Zero Trust security models, operating on the principle that no user or system should be trusted by default, even within the network perimeter.
The Automotive Industry Needs to Act Quickly
The Hyundai breach is not an isolated incident: it’s a symptom of systemic vulnerability in how the automotive industry handles customer data. As vehicles become more connected, more autonomous, and more data-intensive, the volume and sensitivity of information at risk will only increase.
Traditional data security measures, firewalls, access controls, encryption at rest and in transit, are necessary but no longer sufficient. The encryption gap during data processing represents a fundamental vulnerability that sophisticated attackers will continue to exploit.
The question facing automotive executives, IT leaders, and cybersecurity teams is not whether another breach will occur, but whether their organization will be the next one making headlines.
The technology to close the encryption gap exists today. The question is how many millions of customers’ compromised before industry is ready to entertain the need to embrace today’s continuous encryption?
To learn more about continuous encryption with Donoma Seshat, book a no-obligation demo today.
Additional Resources:
Seshat: Data Privacy Preservation for Enterprise
Donoma Puts the Brakes on Data Loss with Next-Generation Privacy-Enhancing Technology
Unlocking Mission Success Through Encrypted Data Processing
Red Hat’s $100M Cyber Breach Problem Is Likely Yours Too
How Privacy Enhancing Technology Could Have Saved TransUnion’s 4.4 Million Victims